Are AWS Certifications worth it? : AWS Solutions Architect - Profassional (SAP) Certification 3

Written by Minhyeok Cha
It's been a while since I've written AWS certification post, so let's get it started.
Question 1.
A company has many AWS accounts and uses AWS Organizations to manage all of them. A solutions architect must implement a solution that the company can use to share a common network across multiple accounts.
The company's infrastructure team has a dedicated infrastructure account that has a VPC. The infrastructure team must use this account to manage the network. Individual accounts cannot have the ability to manage their own network. However, individual accounts must be able to create AWS resources within the subnet.
What combination of actions should the solutions architect perform to meet these requirements? (Choose two.)
ⓐ Create a transit gateway in the infrastructure account.
ⓑ Enable resource sharing from the AWS Organizations management account.
ⓒ Create VPCs in each AWS account within the organization in AWS Organizations. Configure the VPCs to share the same CIDR range and subnets as the VPC in the infrastructure account. Peer the VPCs in each individual account with the VPC in the infrastructure account.
ⓓ Create a resource share in AWS Resource Access Manager in the infrastructure account. Select the specific AWS Organizations OU that will use the shared network. Select each subnet to associate with the resource share.
ⓔ Create a resource share in AWS Resource Access Manager in the infrastructure account. Select the specific AWS Organizations OU that will use the shared network. Select each prefix list to associate with the resource share.
Solutions
This question is about how to you want to manage multiple AWS accounts.
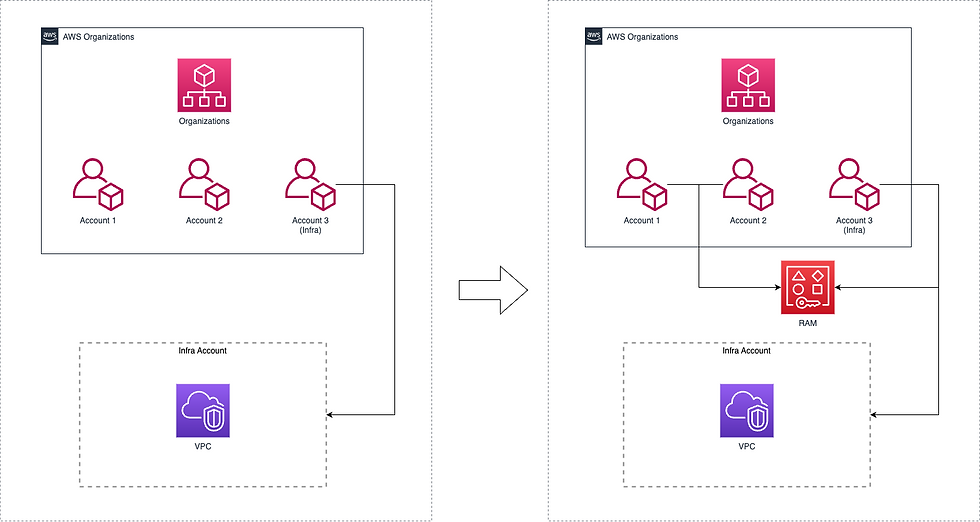
For example, in the picture above, we have two random accounts and one dedicated to infrastructure.
The needs in question are:
These accounts must be used to manage the network. Individual accounts cannot manage their own network.
The individual accounts need to be able to create AWS resources within the subnet.
Since the infrastructure account itself is not designed to manage the network, you can see that the intent is to share permissions with accounts 1 and 2 so that they can manage the VPC subnet resources.
A is wrong - create a Transit Gateway, and as you can see from the architecture of the problem, there is only one VPC mentioned in one account. TG, as you know, is a service that bundles multiple VPCs, so A is not a good fit for this problem.
C is wrong - because building the same environment on each account is not a shared task.
E is wrong - can't share resources via RAM using prefix lists.
D is correct - directly shares the subnets
Therefore, the remaining answers, B & D, are correct and can be solved in AWS Resource Access Manager (RAM).
Correct Answers: B, D
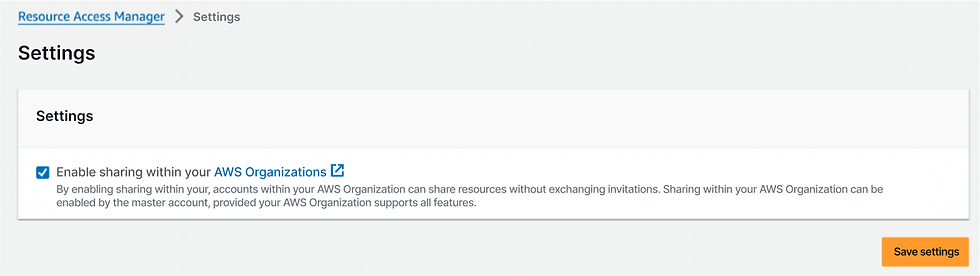
💡 B. Enable resource sharing in the AWS Organizations master account.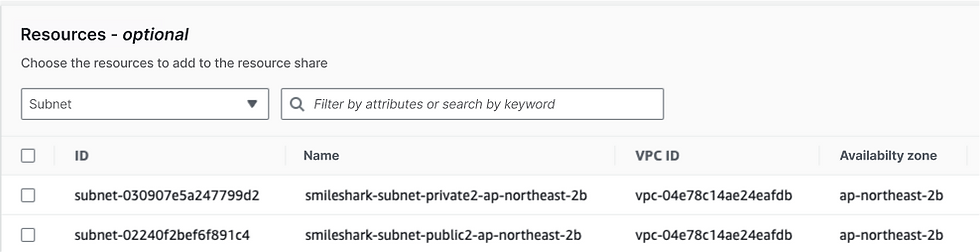

💡 D. Create a resource share in AWS Resource Access Manager in the infrastructure account. Select the specific AWS Organizations OU for which you want to use the shared network. Select each subnet that you want to associate with the resource share.Question 2.
A company wants to use a third-party software-as-a-service (SaaS) application. The third-party SaaS application is consumed through several API calls. The third- party SaaS application also runs on AWS inside a VPC.
The company will consume the third-party SaaS application from inside a VPC. The company has internal security policies that mandate the use of private connectivity that does not traverse the internet. No resources that run in the company VPC are allowed to be accessed from outside the company's VPC. All permissions must conform to the principles of least privilege.
Which solution meets these requirements?
ⓐ Create an AWS PrivateLink interface VPC endpoint. Connect this endpoint to the endpoint service that the third-party SaaS application provides. Create a security group to limit the access to the endpoint. Associate the security group with the endpoint.
ⓑ Create an AWS Site-to-Site VPN connection between the third-party SaaS application and the company VPC. Configure network ACLs to limit access across the VPN tunnels.
ⓒ Create a VPC peering connection between the third-party SaaS application and the company VPC. Update route tables by adding the needed routes for the peering connection.
ⓓ Create an AWS PrivateLink endpoint service. Ask the third-party SaaS provider to create an interface VPC endpoint for this endpoint service. Grant permissions for the endpoint service to the specific account of the third-party SaaS provider.
Solutions
The question has "does not traverse the Internet" in the question, so we're going to eliminate B and C because it involves PrivateLink.
The correct answer for #2 is A, because the perspective is consulting from the consumer's point of view, not the provider's. Account authorization for the endpoint service in D is the provider's responsibility.
Correct Answer : A
We need to create users and providers as per the above solution, so I've set up the following architecture.

On the Provider VPC side, where you have the third-party SaaS application, you must first create an endpoint service.
💡Before creating the endpoint service, it supports network, gateway LB.
The health check of the load balancer should be normal, and the output is shown in the picture below, but since we created the NLB in advance, we'll skip the creation process.1. Provider accounts - Create an endpoint service

2. Provider Account - Add a Consumer IAM ARN

3. Consumer account - Name the endpoint service created in the provider account and send a connection request

4. Provider account - Accept connection request

5. Consumer account - Check status
Question 3.
A security engineer determined that an existing application retrieves credentials to an Amazon RDS for MySQL database from an encrypted file in Amazon S3. For the next version of the application, the security engineer wants to implement the following application design changes to improve security:
✑ The database must use strong, randomly generated passwords stored in a secure AWS managed service.
✑ The application resources must be deployed through AWS CloudFormation.
✑ The application must rotate credentials for the database every 90 days.
A solutions architect will generate a CloudFormation template to deploy the application.
Which resources specified in the CloudFormation template will meet the security engineer's requirements with the LEAST amount of operational overhead?
ⓐ Generate the database password as a secret resource using AWS Secrets Manager. Create an AWS Lambda function resource to rotate the database password. Specify a Secrets Manager RotationSchedule resource to rotate the database password every 90 days.
ⓑ Generate the database password as a SecureString parameter type using AWS Systems Manager Parameter Store. Create an AWS Lambda function resource to rotate the database password. Specify a Parameter Store RotationSchedule resource to rotate the database password every 90 days.
ⓒ Generate the database password as a secret resource using AWS Secrets Manager. Create an AWS Lambda function resource to rotate the database password. Create an Amazon EventBridge scheduled rule resource to trigger the Lambda function password rotation every 90 days.
ⓓ Generate the database password as a SecureString parameter type using AWS Systems Manager Parameter Store. Specify an AWS AppSync DataSource resource to automatically rotate the database password every 90 days.
Solution
This question is looking for a managed service for cryptographic key-levels in AWS. As you can see, there is AWS Secrets Manager and AWS Systems Manager Parameter Store, both of which are services that store key-values.
We need to know about each service before we can solve the problem, but as with any other problem, we can start by looking at the customer need in question
The database must use strong, randomly generated passwords stored in a secure AWS managed service.
Application resources must be deployed through AWS CloudFormation.
The application needs to replace the credentials to the database every 90 days.
The solutions architect generates a CloudFormation template to deploy the application.
B and D are excluded here because the ability to periodically replace credentials is a feature of AWS Secrets Manager, and additionally, they are using resources that are not supported by Cloudformation.

💡 The Parameter Store RotationSchedule resource does not exist, and documentation checks show "RotationSchedule" in AWS Secrets Manager.
💡 AWS CloudFormation does not currently support creating a SecureString parameter type. Then we have to look at the remaining A and C, which is really just a problem of how we trigger the replacement cycle, and the answer is A because we don't have to use Amazon EventBridge, we have our own replacement capabilities.
Correct Answer : A
AWS Secrets Manager refresh cycle

💡 These days, IaCmetas need to be general purpose, so don't use CloudFormation very often. but I included it just in case there's a surprise CloudFormation question on t he AWS exam.Conclusion
I hope the AWS SA certification questions we covered today have been helpful to you. If you have any questions about the solutions, notice any errors, or have additional queries, please feel free to contact us anytime at partner@smileshark.kr.
Comments